How to Determine Which Encryption Algorithm Is Used
Encryption converts data to an unintelligible form called ciphertext. The fact that it is base 64 encoded doesnt tell us much because base 64 is not an encryptionhashing algorithm it is a way to encode binary data into text.

What Is Encryption Explanation And Types Cisco
In these systems an asymmetric algorithm is used to establish a connection.
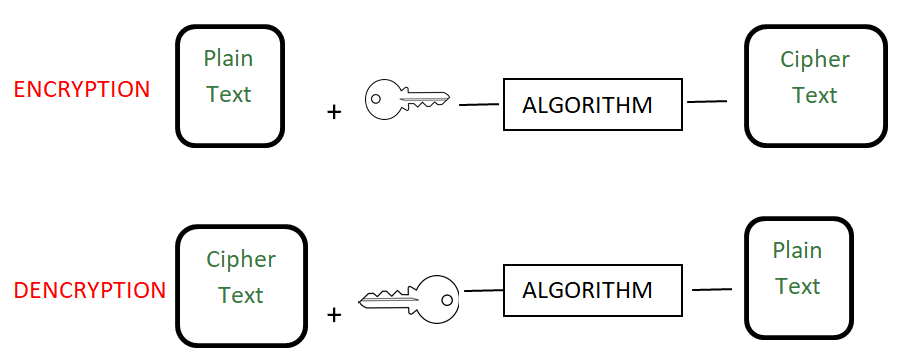
. Cryptographic algorithm that can be used to protect electronic data. On a database instance running with Amazon RDS encryption data stored at rest in the underlying storage is encrypted as are its automated backups read replicas and snapshots. The AES algorithm is.
Encryption algorithm is complex enough to prohibit attacker from deducing the plaintext from the ciphertext and the encryption public key. The method will be used and explained in the step 3 for now copy and include the methods in. Though private and public keys are related mathematically it is not be feasible to calculate the private key from the public key.
This key is then used for establishing symmetric encryption between the two systems. Amazon RDS encryption uses the industry standard AES-256 encryption algorithm to encrypt your data on the server that hosts your Amazon RDS instance. Its not necessary however recomendable to use.
Amazon RDS also supports Transparent Data. In fact intelligent part of any public-key cryptosystem is in designing a relationship between two keys. This method will be used to remove the password from the memory increasing the security of the encryption.
Then a key is transferred between the two systems. Hashing algorithms are just as abundant as encryption algorithms but there are a few that are used more often than others. Decrypting the ciphertext converts the data back into its original form called plaintext.
This means that this block includes one useful piece of information namely that the output is 16 bytes long. The AES algorithm is a symmetric block cipher that can encrypt encipher and decrypt decipher information. We can compare this to the block size of commonly used schemes and figure out what it cant be.
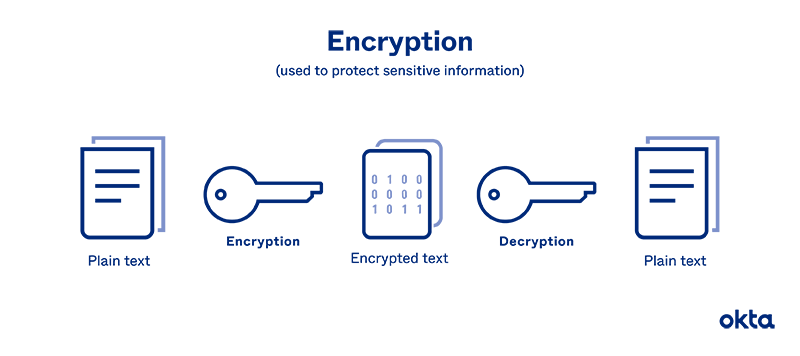
Password Encryption How Do Password Encryption Methods Work Okta
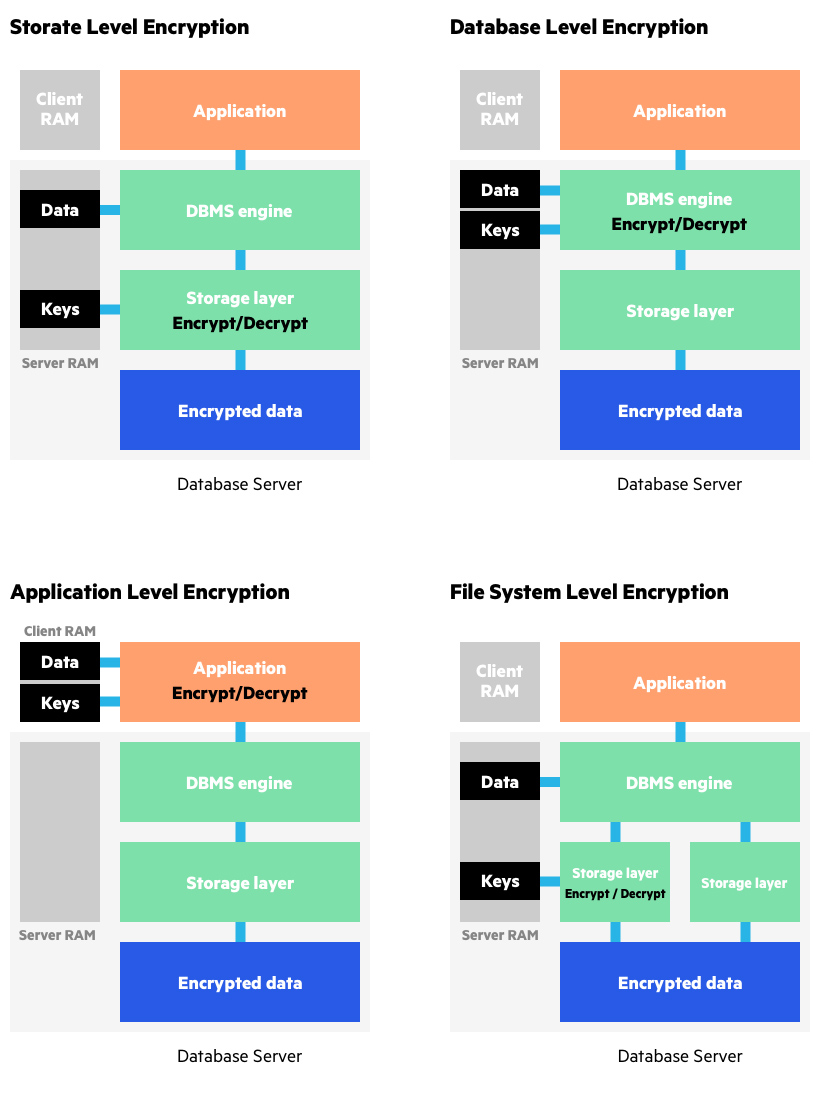
What Is Data Encryption From Des To Modern Algorithms Imperva

Data Encryption Standard Des Set 1 Geeksforgeeks

Symmetric Algorithm An Overview Sciencedirect Topics
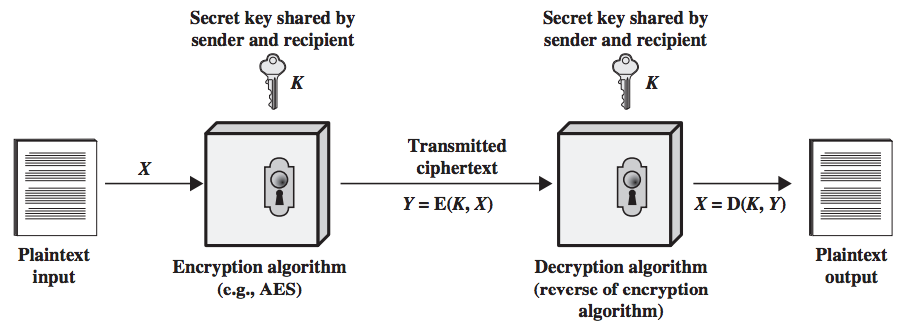
Chapter 2 Classical Encryption Techniques Shichao S Notes

Symmetric Encryption Algorithms Live Long Encrypt Security Boulevard

Encryption Vs Encoding Vs Hashing Geeksforgeeks

Types Of Encryption 5 Encryption Algorithms How To Choose The Right One Security Boulevard
The Best Encryption Algorithms For Cyber Security Rootstrap

5 Common Encryption Algorithms And The Unbreakables Of The Future
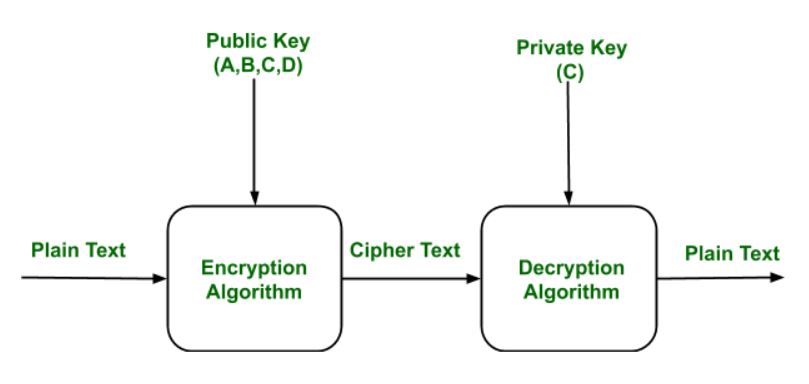
Public Key Encryption Geeksforgeeks

What Types Of Encryption Are There Ico

Hashing Vs Encryption What S The Difference Cybernews

Simplified International Data Encryption Algorithm Idea Geeksforgeeks

Common Encryption Types Protocols And Algorithms Explained

Cryptography If It Didn T Exist We Would Have To Invent It
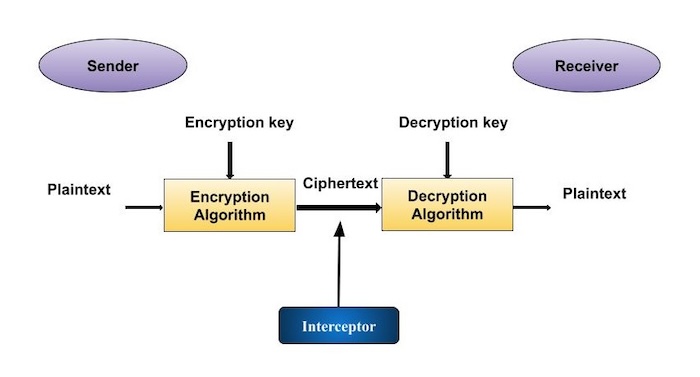


Comments
Post a Comment